
What is a Phishing attack? Stay safe from scams
Posted January 19, 2022 by Angus
Phishing is a cyber-attack method used by cybercriminals. Most of the time, attacks are untargeted; However, targeted cyberattacks against businesses and their employees are becoming more commonplace. Read more about spear phishing here.
The basic aim of phishing is to trick users into believing they’re communicating with a trusted source and to engage with them.
The basics
Phishing can come in many forms: from the most basic to sophisticated cloned websites and phone number Spoofing is a common technique used in email phishing attacks. that provide a false sense of security. Therefore, any engagement involving personal information should be scrutinized at all times.
The most common; basic form of phishing attacks are usually in email format. These emails aim to convince the recipient to enter (or confirm) personal information and/or download malware.
The nature of email means that the list of potential targets is very high. Emails are sent quickly and en masse to millions and if undetected can blend in alongside legitimate email.
As with any spam, the vast majority of Phishing emails will wind up in a spam folder or blocked before even coming close to your mailbox. However, due to the sheer volume of emails sent, a small percentage will make it through and an email will arrive in your inbox.
That’s why it’s always important to double-check any website addresses or email headers. Always keep your wits about yourself when it comes to passwords and sensitive data.
Use the information in this post to help protect yourself from the risk of identity theft.
Prevent Phishing attacks
To help prevent email phishing, you must first understand the goals of a cyber security strategy. Phisher. To either threaten or reassure you into giving them what they want – Your information, Your money and ultimately your identity.
Fortune favours the prepared mind
Louis Pasteur
It’s all about preparation. Deploying software updates promptly could have prevented some of the biggest cyberattacks.
The malware contained within phishing emails can be very destructive to your device. At the start of 2017, the NHS suffered a cyberattack it was vastly unprepared for. This attack used a type of malware called Ransomware, specifically WannaCry. Which infected devices across the NHS, hindering staff’s ability to access patient records and carry out normal operations.
If it wasn’t for the swift actions of an independent security researcher, the NHS’ ability to help critically ill patients would have been severely diminished and potentially held to ransom by cybercriminals.
Although not a targeted phishing incident, malware like WannaCry is mostly distributed through phishing.
We suggest preventing phishing attacks through a Swiss-cheese type model.
This model works by assuming that no single layer of protection can cover everything. Combining multiple layers of technical security measures, a system has better protection.
You can do this by
- Making use of SPF, DKIM & for extra security DMARC records.
- Ensuring all email traffic passes via, a spam filtering system. This labels or discards phishing attempts before reaching a victim.
- Educate yourself, your staff and anyone who uses your systems.
- Keeping devices updated and protected from known vulnerabilities.
- Using additional authentication methods like 2FA applications, which are less vulnerable than SMS authentication methods.
- Unsure about a communication? Get in touch either by phone or our ticketing system.
It’s important to consider that a system is only as strong as its weakest point. Even if you have the best anti-virus software on your device, or the best spam filtering system. If you have a weak password or aren’t paying enough attention you could still fall victim.
Defend against Phishing attacks – Identify Malicious Messages
When considering phishing attacks, it’s important to be able to correctly identify a phishing attempt, this helps to stop the attacker in their tracks and prevent any negative effects.
Knowing this will help you identify a phishing message before you’re “on the hook”. For example, cybercriminals engaged in Phishing attacks tend to use language that infers a sense of urgency.
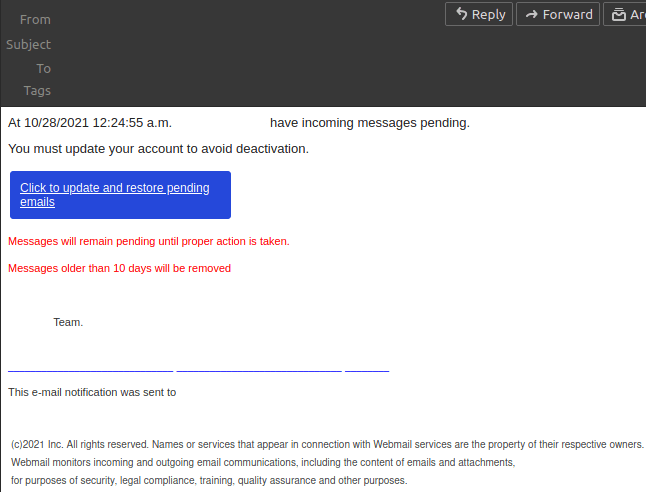
In the past, we have intercepted phishing messages claiming to be cPanel stating that a user’s disk space is low and to act now!
At Unlimited, we don’t apply disk quotas and will never contact you in this way.
This phishing attack directs you to click on a link, leading to a clone phishing website. On this malicious website, you’re prompted to enter your login credentials, which would then allow the attacker to gain access to your cPanel.
These emails are not legitimate and have not been sent from our domain name. If you receive a message like this and are unsure if it is a spoofed message or not, please contact our support team.
Please do not click on any links within these spoofed emails or enter any sensitive information. Phishing campaigns like this are not directed at individuals but rather anyone with similar details, for instance in this case emails were to be sent to generic info@yourdomain.tld addresses.
Also, the only URL that will ever be used alongside your login credentials is
https://www.unlimitedwebhosting.co.uk/client/login
Spot Fakes!
Even with the above steps, it’s important to stay vigilant at all times. In some targeted attacks, fake websites have been set up using a homographic attack style. This means that the URL itself, whilst different, at first glance appears identical. Report a suspicious site to us.
For instance
https://unlimitedwebh໐sting.co.uk/client/login
https://⋃nlimitedwebhosting.co.uk/client/login
Both of these URLs are made to look similar to ours but would lead to other malicious websites.
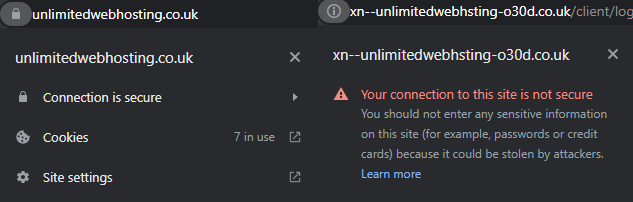
Luckily for us at the moment Nominet the overall controller of .uk and other similarly styled second-level domains such as .co.uk, .org.uk and .gov.uk has limited which of these imposter characters can be used.
Deal with a Phishing attack
As with any attack, Phishing happens in stages. The first stage of a scam is to send either a text message or a phishing email to the victim’s account. If you notice suspicious emails or attachments on or from our service, report incidents to us. You can report phishing emails to the NCSC.
Do not ignore signs of phishing or click on any malicious link to fraudulent websites, as they will likely prompt you to install malware or enter personal details.
If you have passed this first stage, you must act quickly to secure any devices and any accounts with privileged access. You may also want to get in touch with information security professionals who can perform technical security measures to remove any malware or other nasties.
If you have entered personal details (credit card) into a malicious site or lost money to a phishing scam, you must contact ActionFraud helps you report scam incidents.
Spear Phishing Scam
As with lots of internet based-scams, Phishing is becoming increasingly sophisticated. Spear phishing attacks are a type of targeted attack that uses publicly accessible information to tailor scam emails.
This example of a spear-phishing email gives a perfect example of how phishing scams can evade detection by containing minimal content whilst still forcing a sense of urgency on the recipient.
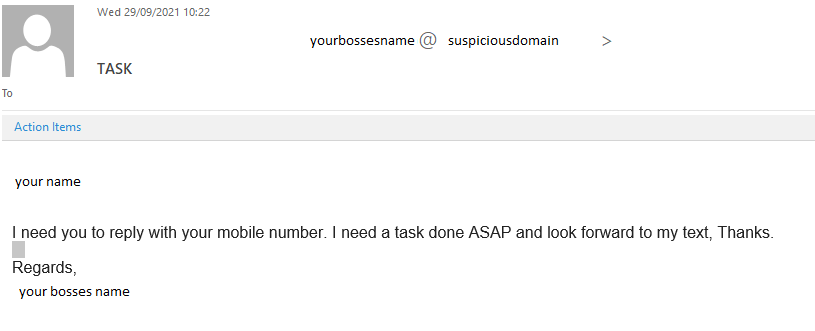
In this case, by getting the victim to reply using their device, they circumvent any workplace security measures. The example is of a common spear phishing campaign but there different ways attackers can exploit this strategy. Its crucial that you help defend against phishing attacks and deny access to sensitive data
Categories: Security
About The Author
Angus is the Website and Content Developer at Unlimited Web Hosting UK where he crafts clear, engaging content optimised for humans.


